In celebration of Cybersecurity Awareness Month, we’re proud to feature a blog post written by Rosh, our cybersecurity intern. This insightful article dives deep into the world of threat actors and hackers, exploring their motivations, tactics, and the real-world impact they have on individuals and organisations alike.
From cybercriminals and state-sponsored attackers to ethical hackers and thrill seekers, the blog breaks down the digital battlefield in a way that’s both engaging and easy to understand. Plus, it offers practical tips to help you stay safe online and reduce your vulnerability to cyber threats.
Whether you’re a tech enthusiast, a concerned user, or just curious about what goes on behind the screen, this is a must-read.
By Rosh Dyquiangco
As technology rapidly advances today, the demand for connectivity and online convenience steadily grows. With that in mind, threat actors are actively scanning and exploiting the lapses in the source code of programs for a multitude of purposes, whether through monetary gain or for political interests. In this article, I will discuss the different types of hackers, threat actors, their motivations behind the screen, and what they aim to achieve. I will also be mentioning tips on how you can stay safe online so that you can minimise the attack surface that threat actors love to sniff out and exploit.
Threat Actors

Figure 1.1 Understanding Threat Actors (Xcitium, 2025)
So, who are threat actors? Threat actors are individuals or groups of people who can disrupt the day-to-day operations of companies or even innocent individuals that just browse from reel to reel on Instagram. Their motivations can range from financial gain to something as silly as chasing thrills. Here are the different types of threat actors:
- Cybercriminals – You’ve heard everything about them in the news, and they populate a large portion of online articles today whenever a large company like M&S gets their confidential company data leaked on online forums. They are the ones that exploit or even blackmail companies in forking over a large amount of ransom money in exchange for their company data to be restored. Most of the time, some of them don’t even follow through and just leak your data regardless. Some of them also love to claim that they possess your data / a virus has compromised your computer and you need to contact them urgently to resolve the problem.
- State-funded threat actors- These guys are probably the most terrifying threat actors that you can ever encounter online. With a large government funding their nefarious activities, they have unlimited resources to work with such as powerful computers that can brute-force multiple character passwords within a few minutes or hours, specially curated software for exploiting companies or even different states with the aim of inciting cyberwarfare or committing acts of espionage, and government cover-ups for the online crimes they commit. With such heavy government backing, they are not to be messed with.
- Cyberterrorists – Cyberterrorists are the ones who are responsible for defacing governments with the aims of enforcing their political, ideological or religious beliefs. They often commit crimes as an act of defiance, with the lot of them not agreeing with the stances of government or company leaders. They love to inflict mass hysteria and stains on the reputation of companies or governments worldwide by gaining access to their websites and replacing genuine articles with hateful, political or downright depravity content. Disruption is the name of the game for these folk.
- Thrill seekers- Often barging into databases, websites or servers for the sake of a dopamine hit, thrill seekers don’t necessarily possess a bad nature like your typical cybercriminal or state-sponsored hacker. They break their way into servers to satiate their curiosity, with the aim of educating themselves in the intricacies and inner workings of networks, computers and the like. They also do not wish to inflict irreversible damage to their targets but their actions which are highly disruptive can lead into them deploying cyberattacks of their own in the future.
- Insider threats – There are two types of insider threats in my perspective, both of which have differing natures depending on their goal. Malicious insiders betray their own company by leaking sensitive information to threat actors. This is their own way of expressing dissatisfaction towards the company itself or the employee services. They might also just simply want to siphon money from the company itself. Incautious insiders are employees who are endangering the company with their lack of care, security and awareness training by downloading software from third-party websites on their work computer or falling victim to phishing emails.
Types of Hackers
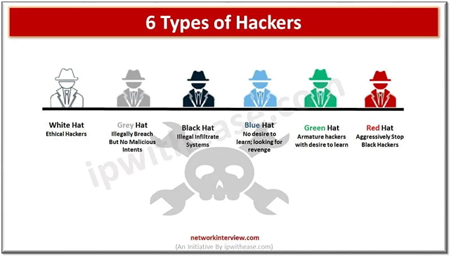
Figure 1.2 6 Types of Hackers (Bhardwaj, 2023)
- Blackhat – Blackhats are the cybercriminals utilizing their skill set for various purposes, often of which leads to their personal or financial gain. Their actions cause massive financial losses and irreversible damage to individuals or companies who are unlucky enough to encounter them.
- Whitehat – Whitehats (also known as ethical hackers) are the good guys of the hacking world. They are often hired by companies to sniff out any existing vulnerabilities within a company’s system.
- Greyhat – Greyhats fall between blackhats and whitehats in a way that they will be accessing sensitive information through unethical means but would never harm their target, instead preferring to inform them about what they can do to improve the security of their systems.
- Greenhat – Another term for greenhorn, they are the newbie hackers who are still learning the ropes of hacking. Aspiring to be future ethical hackers or on the cusp of becoming blackhats, they focus on honing their technical skills
- Bluehat – Hackers who commit crimes as an act of revenge. Unlike cybercriminals who would care about financial gain, bluehats are primarily focused on inflicting damage upon an individual or company’s reputation.
- Redhat – The vigilante hackers who actively shut down blackhat activities no matter the cost. While they are inherently like whitehats on paper by possessing good intentions, they are separated by their ways of breaking into a system. Instead of reporting their findings to local authorities, they take it upon themselves to launch attacks on blackhats.
What you can do when you get hacked

Figure 1.3 Question Mark Figure (HiClipArt, 2019)
- Change your password/s as soon as possible. A healthy password to me is at least 12 characters in length, easily memorable and contains a minimum of 5-6 special symbols. This is to throw off brute-force passwords since they try every combination in the book. Special symbols will help massively in slowing this process down.
- Proactively change your passwords every six months and do not use the same password for every account that you own.
- Let your family and friends know that your account has been compromised.
- Try to activate Multi Factor Authentication on all or most of your accounts if possible. This is a very critical step in maintaining your online safety. The one-time code that gets sent to your device every time you login effectively minimizes the windows that hackers can break into and actively deters them unless they steal the physical device itself.
- Contact your local bank for any fraudulent transaction chargers. Usually, they will be the ones contacting you first about urgent matters like transaction authorization but adopting a proactive approach helps massively.
- Be very careful with the Wi-Fi networks that you connect to. Hackers can employ a very simple yet clever way of impersonating a legitimate network. This hacking technique is called the evil twin attack. Hackers will try to match the details of your local coffee shop Wi-Fi network with a specialized router that they bring with them. The moment you connect to the evil twin network, they can monitor everything you do online and even intercept your transactions and online interactions.
Websites to reach out to if you get compromised
- Your local IT support team – They should be the first point of contact if your work account / device gets compromised.
- Report a scam email – NCSC.GOV.UK – You can report phishing emails to them. Their website offers an easy-to-follow guide of how to report malicious email addresses and offers the numbers of local authorities that can act and investigate as soon as possible.
- Report a breach | ICO – This is the website where you can report data breaches to different fields, from UK GDPR breaches to reporting NIS incidents.
- Have I Been Pwned: Check if your email address has been exposed in a data breach – A website that I often use to check if the email address associated with me or another user has been exposed in a data breach forum somewhere on the internet. Just type in your email address, click check and wait for the results.
- Action Fraud – It is the national reporting centre for fraud and cybercrime in the UK.
References
BHARDWAJ, R., 2023. 6 Types of Hackers [viewed 27 October 2025]. Available from: https://networkinterview.com/6-types-of-hackers/
HICLIPART, 2019. HiClipart – Transparent background PNG cliparts for designers [viewed 27 October 2025]. Available from: https://www.hiclipart.com/
XCITIUM, 2025. Xcitium Software [viewed 27 October 2025]. Available from: https://www.xcitium.com/blog/malware/threat-actors/

